Hi again and thank you for reading.
So, what will this post cover and what could you expect? One of my biggest struggle is to scope things and not get carried away. So initially I wanted the first post to cover both the strategic and technical aspect of setting up and activating your first O365-tenant and Azure subscription. Covering the basics. Touching into topics like a little bit of planning and strategy, anchoring, lobbying, budgeting, licenses, branding, custom domain names, PIM and roles, MFA…aaaand there you go – I’m already building a humongous blogpost that probably would loose you halfway because of the length and complexity, and I haven’t mentioned all the topics yet…
So I will have to divide it into several parts. This first part will not get technical. But the next ones will be, I promise!
What I will try to do with these posts is to give a general idea of how I would do it, a little bit of tips, tricks and why to do it the way I suggest (don’t worry, I use best-practices where I can, if not I will underline that 😉) – and underneath every topic I will link to a more in-depth-post on how to set up, or do, that particular thing. That would mean that if you read this post right now when it’s fresh, it may not contain any link to the “how-to” because I haven’t made that yet. But if you are from the future (what’s it like there, do we get flying cars?!?!), I will probably and hopefully have the how-to’s ready as well and you can get both a more complete overview as well as an in-depth insight in all the possibilities and how to set it up. And even better; WHY you should do it that way.
As I wrote in my disclaimers (who reads disclaimers anyway?) I do not imply that my way is the correct way, but often it will be. Why? Because it is what is suggested as “best-practice” by most of the people who really knows what they are talking about. But I am more than happy to discuss the content on here, do not be afraid to ask questions or to disagree with anything. I would love it actually! It would be a big possibility that we both learned something new, and I will tell you right away that I would not be afraid to update or change the content if I was wrong the first time.
The scenario
Firstly, we will make ourselves a bit of a fictional scenario, so we have something relatable and some context to the rest of the topics. This is all fictional and as the disclaimer said, this is not reflecting current or earlier environments or persons in any form or matter. Consider this as a fictional worst-case scenario. And if you can relate to some aspects in scenario, don’t be scared (because I don’t think you are alone in that matter), maybe this could help you get out of those unwanted situations? If you can relate to it all and don’t see any problems, you have some work to do! 😊
We will try to setup an environment for a company called Prottecio. Prottecio sells something to their customers and they have 1 main office in Norway where the leader group, HR, IT and marketing resides and 3 sales&support offices located in Las Vegas(US), Isle of Islay (Scotland) and Piemonte (Italy), because the CEO loves to play poker, drink smokey whisky and quality Italian cuisine and wine. It consists of approximately 100 users where we have an IT-team of 5, and one of the IT guys is running the show.
I will not cover a lot of on-premise stuff in this blog as for now (who knows, maybe later), but for the scenario we can say that Prottecio is currently running AD on premise along with locally hosted Exchange (outdated off course…), file shares (which of course has no RBAC, no routine of version handling on the files, a lot of documents contains sensitive customer data, user data, shared passwords and so on), and all the works. The main communication internally in Prottecio is by mail.
One big issue with the data in AD is that it is not fresh. Prottecio has approximately 100 users, but in AD we have over 200 users, a lot of them not working there anymore, and those who still works there may have changed both office-locations and job positions. It also contains a lot of devices that are not in use anymore and there is no naming convention on users, devices or security groups. Today they have no local endpoint management system, windows-patching is all over the place and managing phones and tablets is non-existing. Most of the third-party-applications is installed on the computers by the users themselves (who is off course local admins) and they are never patched. Most of the users have a dedicated computer, but there are some shared as well. They all have mobile phones (both company owned and BYOD).
With the pandemic happening a lot of the users have worked from home or hotels and they use whatever network available to them, shared, mobile and so on. To get access the legacy applications and locally resources they use non-secured RDS without VPN. Most of them is using legacy protocols to access mail from their mobile devices, but also because of the old Outlook-version on the computers which has never been updated. None of the employees have ever heard of MFA, ransomware, phishing or shadow-IT before – in-fact some of them think they are fancy names on drinks…
The members of the IT-team have one user-account each which they use for administrating AD, installing cool features and plug-ins on the servers, and sending their e-mail. And it is all done from the same computer(s).
Let us also add that there is in no form or matter any form of strategic document from the leaderboard on how things should be either, because all of this is IT’s responsibility, right? Nothing in IT or the rest of the organization is very well documented either. Since we won’t cover to much setup on-prem (at least yet), we will assume that they hired some skilled people to do their networking, so they actually have segmented network (servers are separated from the user computers, we have an own BYOD network, guest network), good wireless features on all locations, awesome firewalls – and so on.

Suddenly, one day, one of the big competitors of Prottecio is taken down by ransomware. All their systems is non-responsive, alle their data is encrypted and for sale on the dark web. That same night the CEO of Prottecio and the CEO from the competitor (which happens to be both neighbors and friends) is having a good talk. The next day, the CEO from Prottecio calls in the IT-guy (us) and tells us we must change things a bit. Prottecio shall not be taken down the same way as the competitor did – we should be 100% safe!
Can we ever be 100% safe? No. But what if we tried to be better than the “neighbors”? Maybe we won’t get caught first? And if we successfully implement a good strategy for detect, respond, and recover we can minimalize both risk and impact of being hit?
The only pointers we got from the CEO is that he wants to move what services we can to the cloud (he has invested heavily in Microsoft stocks) and secure them, we need to start patching both devices and apps, he heard someone talk about Zero-Trust on the radio on his way to work so he wants that, and he needs to have reports on the security status at a steady basis.
Where do we begin?
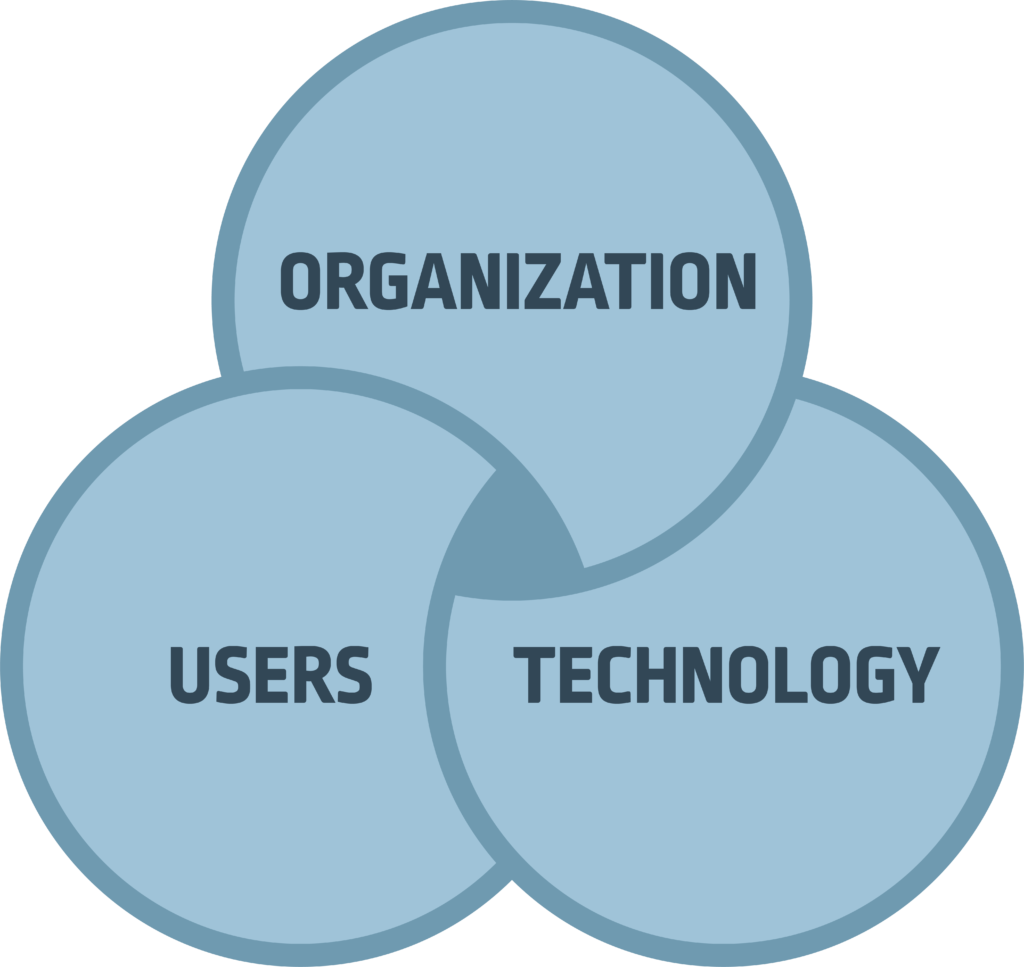
Where do we start? With a plan. And a list, I really like lists! (Don’t get me started on Planner or TO-DO…) I want to stress to you that how we help Prottecio to improve may not be the optimal route for you to go. This is just an example on how we could do it. And by going down this route how we should implement best practices in the solutions. But since I talked about highlighting what I like to call the tri-unity in this blog, organization-users-technology, I will try to do just that. Because we can’t solve the CEO’s challenges just with technology or by buying solutions – we need to take some steps back and see all the connections.
After a long evening with a couple of nice whisky’s the IT-team comes back to the CEO with their list and tells him that they need the following to follow up on his requests and wishes;
- Organization
- Involve the leader group and stakeholders early and explain that we need the following
- A good overview and plan for the enterprise architecture
- A good overview and plan for the management model and responsible roles
- Realize that security is not an IT-challenge, no technical solution can secure an organization alone
- Help to design and adopt a good framework and strategy for security
- Enforce and implement security in all services and work processes and make it a mentality instead of an implementation mindset
- Help to change the culture in the organization
- Help to build a solid communication platform to share important information in the organization.
- Help to produce standardized internal user manuals, guidelines and regulations which cover topics such as
- Acquisition of services, solutions, and applications to support local and international regulations such as privacy, GDPR, information security+++
- Usage, caution, and restrictions of using digital devices and the potential risk of exposing sensitive data to unauthorized persons
- Help to make a good strategy for skills development and adopt a framework for this
- Facilitate and encourage (and in some categories demand) all the employees to increase their understanding and skills in their field of work and on their systems – but also on a general basis considering organization culture, digital workspaces and basic security
- Help to establish Champions in the organization to
- Remedy a great number of potential and unnecessary user support issues on the spot
- Perform as instigators for changes and drive adoption in their department
- Help the users and company to increase productivity and efficiency
- Be a valuable connecting link between IT and the end-users
- To not treat IT as a cost center. We can’t buy a magical solution to solve the challenges, but some remediations will lead to some costs in form of licenses, specific solutions and costs connected to workshops, skills development, hiring external help and competence, and so on. If Prottecio doesn’t have the needed competence to solve it’s issues in-house, we need to employ, hire or buy it.
- According to Microsoft this is a common “antipattern”, treating IT as not adding value to the company instead of being an enabler. (https://learn.microsoft.com/en-us/azure/cloud-adoption-framework/antipatterns/organize-antipatterns#antipattern-treat-it-as-a-cost-center)
- Involve the leader group and stakeholders early and explain that we need the following
- User
- Involve the users early and explain that we need the following
- To participate in the security strategy – no one can be elective or choose to be a part of it or not – security is a shared responsibility and involves everyone.
- To participate in the change of culture in the organization – we work as a unity and we need everyone to work for a common goal.
- To involve themselves in skills development, both in their everyday systems and field of work, but also on a general basis, especially security.
- To understand that some work processes will be challenged and maybe forced to change if they do not meet the security standards the company needs and are working towards
- To report, at once, if they experience anything out of the ordinary that could be a potential security threat – both digital and humane.
- Involve the users early and explain that we need the following
- Technology
- Establish a security strategy based on best-practice – in this scenario we will take a look at the ground pillars from NSM (The Norwegian National Security Authority), which is fairly similar to, for instance, the NIST Cybersecurity Framework. (LINK – Norwegian only!)
- Adopt a security framework and stick to it, so we can measure improvement over time
- Adopt and implement a Zero-Trust mentality and strategy so we can
- Identify our assets, environments, and risks
- Protect our identities, endpoints, network, apps, data and infrastructure
- Detect anomalies
- Respond to the threats
- Make and test a plan to Recover if something really dirty hits the fan
- Implement automated (where we can), standardized, secure, and well-documented solutions to support the digitalization and work processes in the organization
- Adopt and implement a work methodology that makes the whole IT-department (us) able to perform the necessary planning, strategy, changes, and documentation.
- Follow best-practice as far as we can, but also adopt when this will not suit our enviroment.
- Establish a security strategy based on best-practice – in this scenario we will take a look at the ground pillars from NSM (The Norwegian National Security Authority), which is fairly similar to, for instance, the NIST Cybersecurity Framework. (LINK – Norwegian only!)
I am super-happy to announce that I have “awakened the desire to write” on some super-skilled friends of mine with a lot of expertise in some of the above mentioned fields, who will make some guest apperances in the near future. When those posts are published I will link to them in the above topics from the list.
But let’s call it a day for Part 1. In Part 2 our SUPER IT-TEAM will get hands on setting up the tenant and a lot of cool stuff related to that. We will cover topics such as subscriptions and licenses, password manager, tier-modelling, admin-portals, company branding, verifying domains, breakglass-accounts, MFA, conditional access, PIM, passwordless and so on. In other words, another short blogpost, we have only covered the tip of the iceberg… 😉
Going further we also need to make a plan and decide how we would implement our identities in AAD, secure them, authenticate them, audit them and so on. I can’t wait! 😊
Until next time, spread the word – sharing is caring!

